前言
这题给我干懵逼了,unicorn基地址一开始设置成0x400000会无法进入下一步?我打印出寄存器,才发现EAX是0x119c!之后访问0x119c地址必然报错!还得把基地址改成0x0,具体原因因为懒得调试分析了,明天再研究.
程序逻辑
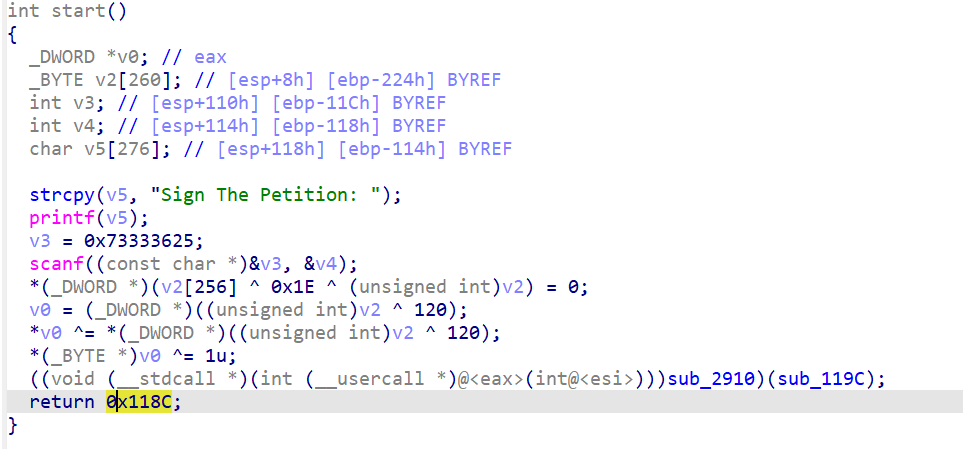
其实就是不断递归。而且每次验证一位,匹配就进入下一层递归。而且每次递归结构都基本相同,找个特征就能全部匹配。好的,那就直接用unicorn无脑一把梭了。
注意!!!
记得把scanf和printf给patch掉,因为这些函数并没有加载到虚拟地址上,调用必然会报错!
其他没什么好注意的,会一点unicorn基本语法就行。
EXP!
from unicorn import *
from capstone import *
from unicorn.x86_const import *
import binascii
param=0
flag=b''
def show_reg(uc):
print("EAX", hex(uc.reg_read(UC_X86_REG_EAX))[2:].upper().zfill(8))
print("EBX", hex(uc.reg_read(UC_X86_REG_EBX))[2:].upper().zfill(8))
print("ECX", hex(uc.reg_read(UC_X86_REG_ECX))[2:].upper().zfill(8))
print("EDX", hex(uc.reg_read(UC_X86_REG_EDX))[2:].upper().zfill(8))
print("ESP", hex(uc.reg_read(UC_X86_REG_ESP))[2:].upper().zfill(8))
print("EBP", hex(uc.reg_read(UC_X86_REG_EBP))[2:].upper().zfill(8))
print("ESI", hex(uc.reg_read(UC_X86_REG_ESI))[2:].upper().zfill(8))
print("EDI", hex(uc.reg_read(UC_X86_REG_EDI))[2:].upper().zfill(8))
print("EIP", hex(uc.reg_read(UC_X86_REG_EIP))[2:].upper().zfill(8))
def hook_scanf(uc,address,size,data):
#print(hex(address))
if address==0x110b:
#show_reg(uc)
edi=uc.reg_read(UC_X86_REG_EDI)
uc.mem_write(edi,flag)
#print(uc.mem_read(uc.reg_read(UC_X86_REG_EDI),10))
def hook_code(uc,address,size,data):
global param
com=bytearray(b'1\xc0\x83\xf0\x01')
code = uc.mem_read(address,5)
if code==com:
param=param+1
def init():
uc = Uc(UC_ARCH_X86, UC_MODE_32)
address = 0x0 # 运行地址
stack_addr = 0x10000 # 堆栈地址
# data_addr = 0x20000 # Data的数据
uc.mem_map(address,2*1024*1024)
with open ("Petition","rb") as f:
code =f.read()
uc.mem_write(address,code)
uc.reg_write(UC_X86_REG_EIP, 0x1040)
uc.reg_write(UC_X86_REG_ESP, stack_addr)
uc.mem_write(0x10C6,b'\x90\x90\x90\x90\x90')
uc.mem_write(0x110B,b'\x90\x90\x90\x90\x90')
uc.hook_add(UC_HOOK_CODE,hook_scanf)
uc.hook_add(UC_HOOK_CODE,hook_code)
try:
uc.emu_start(0x1040,0x29C4)
except Exception as e:
print(e)
uc.emu_stop()
tmp=b''
for i in range(42):
for j in range(32,128):
flag=tmp+bytes([j])
print(flag)
param=0
init()
if(param==i+1):
tmp+=bytes([j])
break
init()
print(tmp)
#b'flag{96c69646-8184-4363-8de9-73f7398066c1}'
_%7B%25X@D.gif)


评论区